PDF) OWASP TOP 10 VULNERABILITY ANALYSES IN GOVERNMENT WEBSITES | Dr. N. J. Patel and Deven Pandya - Academia.edu

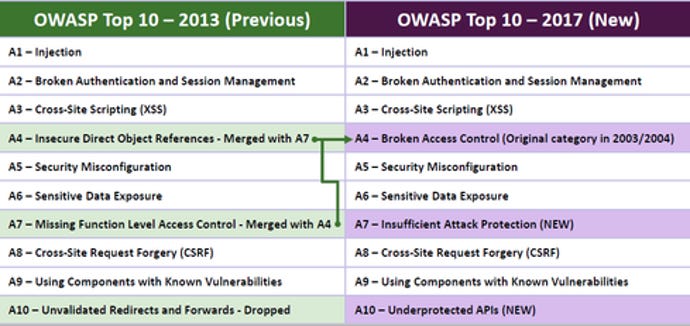
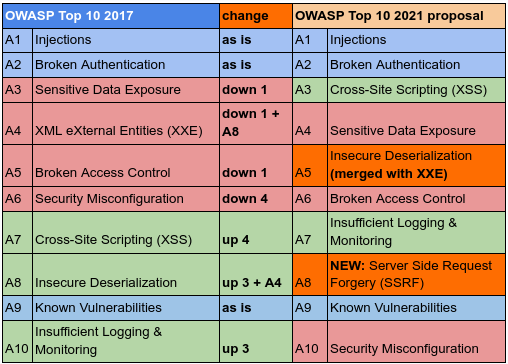
Web Security and the OWASP Top 10: The Big Picture - Paperpicks Leading Content Syndication and Distribution Platform
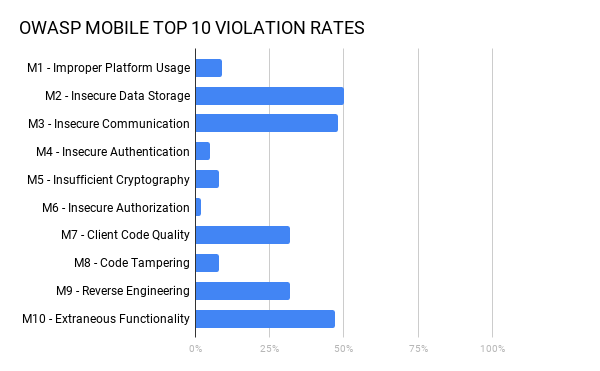
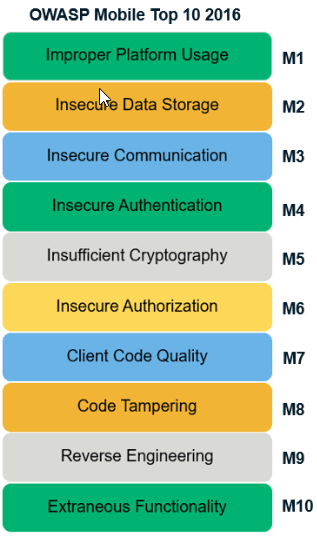
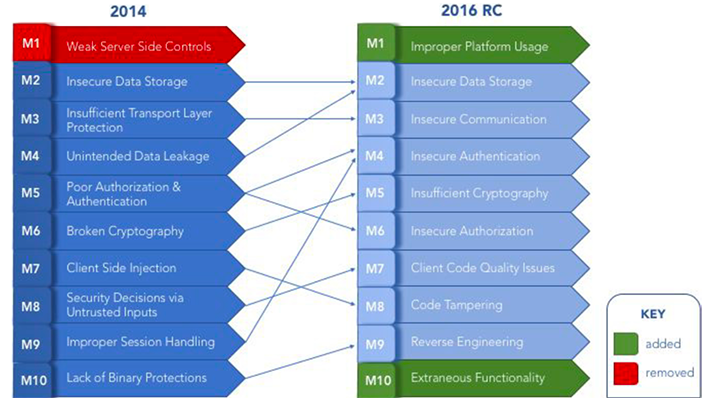
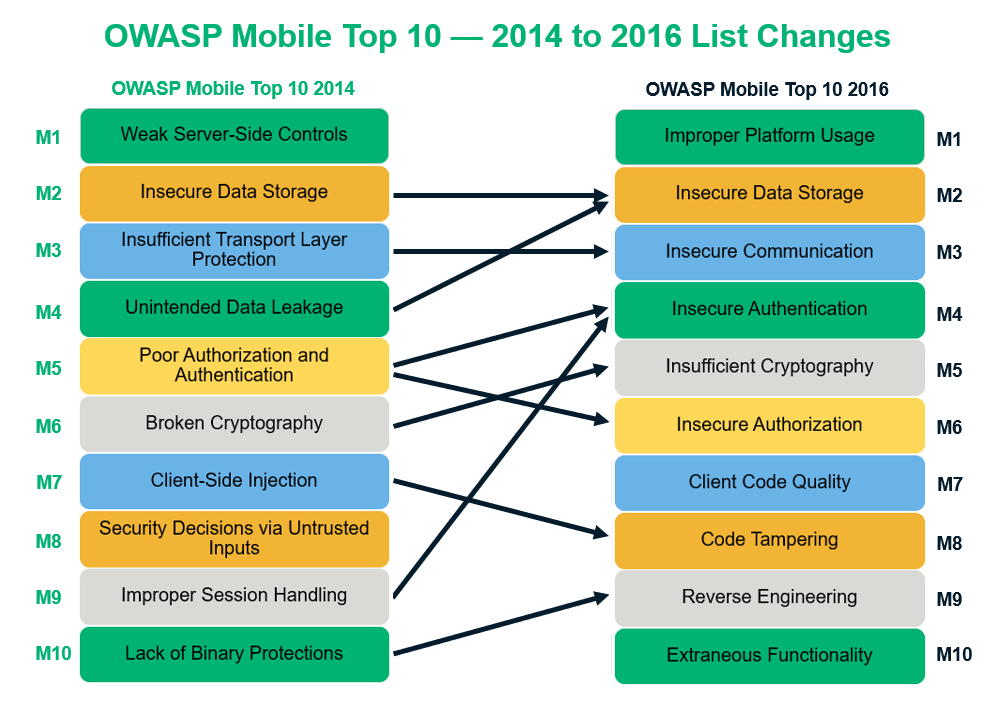
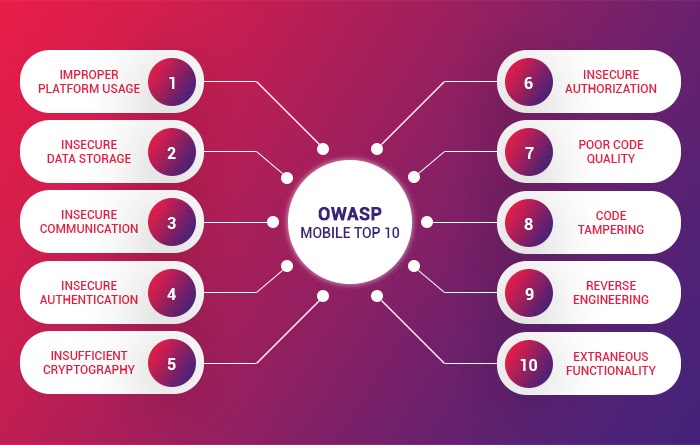
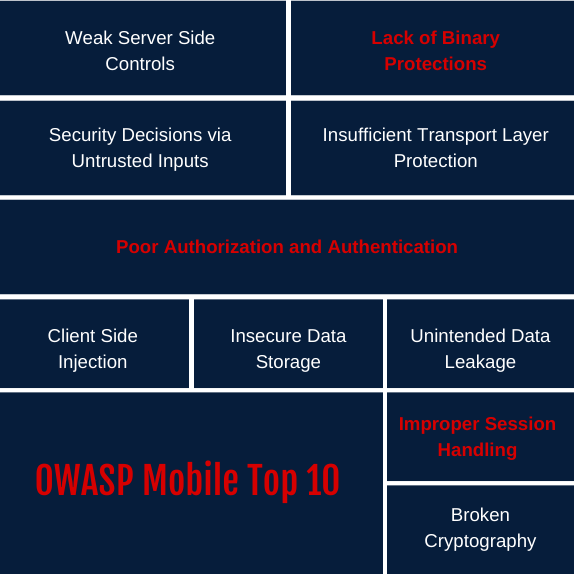
OWASP mobile top 10 security risks explained with real world examples | by Kristiina Rahkema | The Startup | Medium